-
Docker Volume Permissions: Mismatch Between Host UID and Container UID
When you have a Docker container with a user that has a different UID from the one on your host, mounting a volume and accessing the files can result in permission issues.
Read more… -
Postgres Data Types, Sizes and Alignment
How much storage does a single row in a Postgres table take?
Read more… -
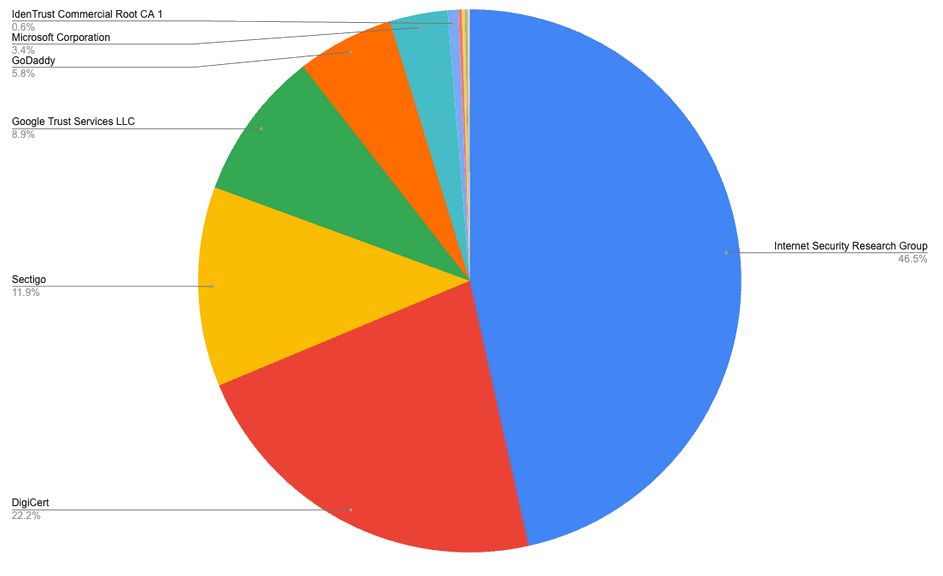
Remove All CAs From Linux Trust Store
On Security Now! podcast #951, Steve told us that 7 organizations in the PKI are responsible for minting upwards of 99% of all existing certificates. (Possible original source.)
Read more… -
Cookies
Under what circumstances cookies are accepted or rejected by user agents and send back to web servers can be a bit confusing. Let’s experiment a bit.
Read more… -
Create Self-Signed TLS Cert With Wildcard
Let’s create a self-signed certificate that contains a wildcard Subject Alternative Name (SAN).
Read more… -
Overwrite File Without Truncating
In Bash, when you open a file for writing, the file gets truncated. However, there is a way to open a file for both reading and writing at the same time.
Read more… -
Bash's exec Replaces Shell
This is a quick look at Bash’s
Read more…execbuiltin with a simple example. -
Commands in Pipelines Are Executed in Subshells
Let’s have a look at another one of those gotchas that can bite you while scripting in Bash: processes that are part of a pipeline all run in subshells.
Read more… -
Create Persistent Connections to Processes Using FIFOs
In this post, we are going to make a Bash script interact with an HTTP server and have multiple exchanges using the same connection by leveraging named pipes/FIFOs.
Read more… -
Upgrade Password Hashing Method for Existing Users
When you’ve been using the same Linux system for a while, you might want to upgrade the password hashing methods used. This article explains how to discover the methods supported by your system, set the preferred method and then upgrade the password hashes to make use of the new hashing method.
Read more…